
Information Security
Information Security Policy and Vision
1.Enhance employee awareness.
2.Prevent information leaks.
3.Implement routine O&M.
4.Ensure service availability
Information Security Objectives
1.Organize information security training to increase employees’ information security awareness and strengthen their knowledge of related responsibilities.
2.Protect information on the Company’s business activities from unauthorized access and modification to ensure its accuracy and integrity.
3.Conduct regular internal and external audits to ensure that all required operations are implemented.
4.Maintain a high level of system availability for the Company’s critical core systems.
Structure and Responsibilities of the Information Security Committee
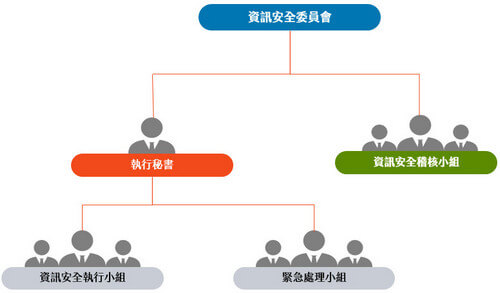
Information Security Committee
- The Committee is composed of a task force headed by the Chief Information Officer of the Company who serves as the convener.
- The heads of each business department are members of the Committee. If the head of a department is replaced, a replacement must be immediately assigned to process handover procedures.
Executive Secretary
- The role of the Executive Secretary shall be filled by a member of the Information Technology Department designated by the convener.
Information Security Execution Team
- The Team is composed of a task force with a Team Leader and members assigned by the Committee. They are responsible for planning and executing information security operations.
Emergency Response Team
- The Team is composed of a task force with a Team Leader and members responsible for key business procedures assigned by the Committee.
Information Security Audit Team
- The team members are assigned by the Information Security Committee to take charge of the implementation of the information security management system.
Specific Information Management Measures
The Company established the Information Security Committee in April 2018 to enhance information security management. The Committee is responsible for reviewing the information security governance policies of the Company and its subsidiaries and overseeing information security management. We also hold regular ISMS management review meetings to review information security and governance-related issues and make continuous improvements to ensure the formulation and applicability of information security policies.
The Chief Information Officer of the Company is responsible for the governance, planning, supervision, and implementation of information security operations to construct comprehensive information security defense capabilities and information security awareness of employees.
Our information security strategy focuses on information security governance, legal compliance, and the use of technologies, from systems to technology and from personnel to organization to improve comprehensive capabilities in information security.
In view of emerging threats in information security such as DDoS (Distributed Denial of Service) attacks, ransomware, social engineering attacks, and counterfeit websites, the Company regularly pays attention to information security issues and plans response strategies. We organize exercises for different information security scenarios to strengthen the response of our employees so that we can detect and block attacks immediately. We also organize regular information security audits (Communication and Operation Management System) such as vulnerability scanning or penetration tests to make sure that the information system and network environment meet safe implementation standards.
As information security insurance is a new type of insurance policy and involves issues such as the information security rating and inspection institutions, claim forensic institutions, and conditions under which claims are not provided, the Company is currently considering whether the purchase of information security insurance is necessary. Our future goals are to complete information security regulations, conduct regular information security assessments, and obtain international information security certifications. We will continue to strengthen information security protection and establish joint defense mechanisms, especially in the training of talented information security personnel. The Company will regularly announce information security policies and organize arrange information security training every year.
The Chief Information Officer of the Company is responsible for the governance, planning, supervision, and implementation of information security operations to construct comprehensive information security defense capabilities and information security awareness of employees.
Our information security strategy focuses on information security governance, legal compliance, and the use of technologies, from systems to technology and from personnel to organization to improve comprehensive capabilities in information security.
In view of emerging threats in information security such as DDoS (Distributed Denial of Service) attacks, ransomware, social engineering attacks, and counterfeit websites, the Company regularly pays attention to information security issues and plans response strategies. We organize exercises for different information security scenarios to strengthen the response of our employees so that we can detect and block attacks immediately. We also organize regular information security audits (Communication and Operation Management System) such as vulnerability scanning or penetration tests to make sure that the information system and network environment meet safe implementation standards.
As information security insurance is a new type of insurance policy and involves issues such as the information security rating and inspection institutions, claim forensic institutions, and conditions under which claims are not provided, the Company is currently considering whether the purchase of information security insurance is necessary. Our future goals are to complete information security regulations, conduct regular information security assessments, and obtain international information security certifications. We will continue to strengthen information security protection and establish joint defense mechanisms, especially in the training of talented information security personnel. The Company will regularly announce information security policies and organize arrange information security training every year.